Web Application Penetration Testing
NetSPI pentests your web applications wherever they are hosted. We employ manual and automated penetration testing processes using commercial, open source, and proprietary security testing tools to evaluate your web application from the perspective of anonymous and authenticated users.
Improve Application Security
NetSPI’s web application penetration testing reduces organizational risk and improves application security
Now that perimeter network security is more evolved, web applications are being targeted as one of the weakest links. NetSPI identifies security vulnerabilities in web applications that make your organization susceptible to external or internal security threats.

Our penetration testers find 20% more vulnerabilities by using our Resolve™ platform and proven pentest methodology.

What Does NetSPI Test For?
- Injection
- Broken authentication
- Sensitive data exposure
- XML external entities (XXE)
- Broken access control
- Security misconfiguration
- Cross-site scripting (XSS)
- Insecure deserialization
- Components with known vulnerabilities
- Insufficient logging and monitoring
Web Application Penetration Testing Service
During our web application penetration testing service, NetSPI pentests your web application for security vulnerabilities and provides actionable guidance for remediating the vulnerabilities and improving your organization’s application security risk posture.

Anonymous Testing
- Non-credentialed user
- Tests application and system layers
- Multiple scanners
- Manual verification

Authenticated Testing
- Credentialed users by role
- Automated and manual processes
- Elevate privileges
- Gain access to restricted functionality
- Manual verification
TERMS TO KNOW
What is the OWASP Top 10?
In addition to identifying application logic weaknesses, NetSPI’s web application security testing service targets OWASP Top 10 web application vulnerabilities.
The OWASP Top 10 is a list of the most critical cybersecurity risks to web applications, identified by an industry consensus. Adopting the OWASP Top 10 in your software development and application security testing processes is a strong step in improving application security for your business, your partners, and your customers.
OWASP Top 10
| A1 | Broken Access Control |
| A2 | Cryptographic Failures |
| A3 | Injection |
| A4 | Insecure Design |
| A5 | Security Misconfiguration |
| A6 | Vulnerable and Outdated Components |
| A7 | Identification and Authentication Failures |
| A8 | Software and Data Integrity Failures |
| A9 | Security Logging and Monitoring Failures |
| A10 | Server-Side Request Forgery |
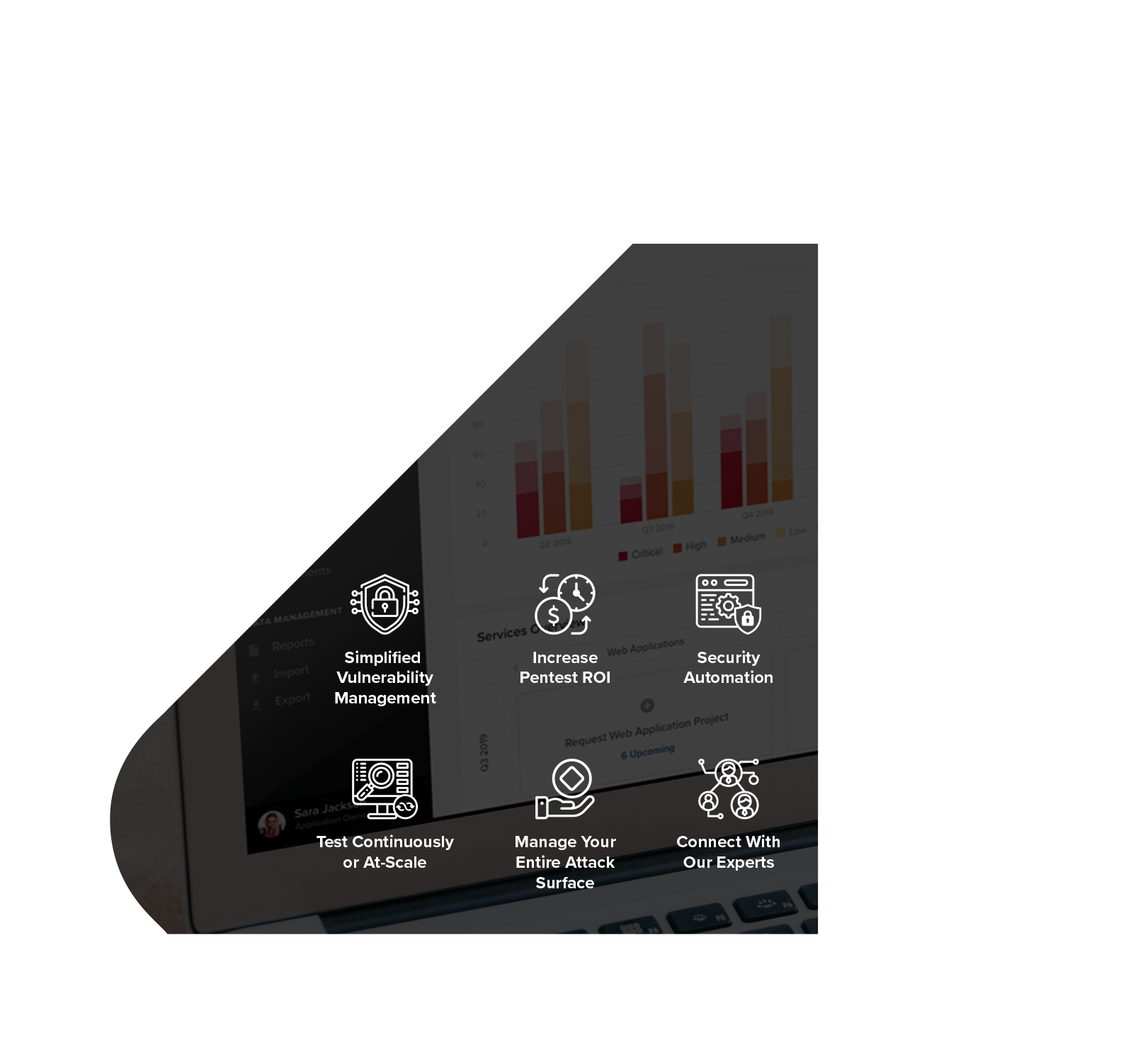
Powered by Resolve™
Web application pentesting engagements are managed and delivered through Resolve, NetSPI’s vulnerability management and orchestration platform. Resolve elevates your vulnerability management and pentesting program.

Web Application Pentesting Resources
ATM Pentesting Research and Tools
Learn about penetration testing on our blog, our open source penetration testing toolsets for the infosec community, and our SQL injection wiki.


