Azure Penetration Testing
Our Azure penetration testing service identifies cloud configuration and other security issues on your Azure infrastructure and provides actionable recommendations to improve your Azure cloud security posture.
Improve Azure Security
Reduce organizational risk and improve cloud security
Whether you are migrating to Azure, developing cloud native applications in Azure, using Azure Kubernetes Service (AKS), or pentesting Azure annually for compliance, penetration testing your Microsoft Azure infrastructure helps you ensure your cloud is secure.
During Azure penetration testing, NetSPI identifies high-impact vulnerabilities in your Azure services, including applications exposed to the internet.

Gartner estimates up to 95% of cloud breaches occur due to human error, such as misconfigurations, and attackers continuously scan the internet to find these exposures.
Azure pentesting also identifies exposed credentials, excess privileges, and security misconfigurations in your Azure Active Directory integration. These security issues can lead to the compromise of your Azure infrastructure and enable an attacker to expose sensitive data, take over Azure resources, or pivot to attack your internal network.
Deliverables include an Azure penetration testing report with prioritized vulnerabilities and actionable guidance to help you reduce risk and secure your Azure attack surface.
Azure Pentesting Techniques
Our Azure penetration testing service includes a cloud services configuration review and external and internal penetration testing techniques, such as:
- System and services discovery
- Automated vulnerability scanning
- Manual verification of vulnerabilities
- Manual web application pentesting
- Manual network protocol attacks
- Manual dictionary attacks
- Network pivoting
- Domain privilege escalation
- Access sensitive data and critical systems
What to Know
Scanning internet-facing cloud resources is a high priority, but a complete cloud security assessment that tests the hardness of your Microsoft Azure infrastructure requires more steps to:
- Discover all internet-facing assets a hacker could find as potential entry points into your Azure account
- Identify attack surfaces exposed by cloud and Active Directory integration
- Identify known and common vulnerabilities on internet-facing assets and web applications
- Identify confidential data exposure on publicly available resources
- Identify less severe vulnerabilities that can be chained together to obtain unauthorized access to other systems, applications, and sensitive data
- Verify findings using manual Azure penetration testing techniques and removing false positives
- Deliver actionable guidance for how to remediate verified vulnerabilities
Do I need to get Azure penetration testing approval from Microsoft?
No. As of June 2017, Microsoft no longer requires pre-approval to conduct a penetration test against Azure resources. Microsoft explains, “We don’t perform penetration testing of your application for you, but we do understand that you want and need to perform testing on your own applications. That’s a good thing, because when you enhance the security of your applications you help make the entire Azure ecosystem more secure.” NetSPI’s penetration tests comply with Microsoft Cloud Unified Penetration Testing Rules of Engagement.
Why do I need to use annual penetration testing processes in addition to multiple toolsets during Azure penetration testing?
NetSPI Critical Vulnerability Discoveries Found Through
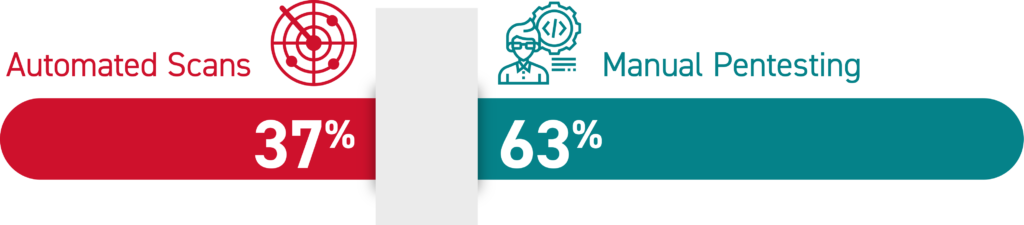
NetSPI’s External Pentesting Identifies

Powered by Resolve™
Azure penetration testing service engagements are managed and delivered through Resolve, NetSPI’s vulnerability management and orchestration platform. Resolve elevates your vulnerability management and pentesting program.

Azure Penetration Testing Resources
Watch this on-demand webinar where Karl Fosaaen explores common initial Azure access vectors, along with a handful of escalation paths for getting full control over an Azure tenant, and some techniques for maintaining privileged access.
If your organization uses a cloud platform, you may use AWS or Microsoft Azure. No matter which platform you’re on, each cloud platform has its own security considerations.
Read this blog from cloud expert Karl Fosaaen for an overview of how to use each option in the Get-AzurePasswords module in MicroBurst. As each targeted service in the script has a different way of getting credentials, this blog can help you understand how things are working.
