Sam Kirkman
WP_Query Object
(
[query] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "134"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "134"
[compare] => LIKE
)
)
)
[query_vars] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "134"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "134"
[compare] => LIKE
)
)
[error] =>
[m] =>
[p] => 0
[post_parent] =>
[subpost] =>
[subpost_id] =>
[attachment] =>
[attachment_id] => 0
[name] =>
[pagename] =>
[page_id] => 0
[second] =>
[minute] =>
[hour] =>
[day] => 0
[monthnum] => 0
[year] => 0
[w] => 0
[category_name] =>
[tag] =>
[cat] =>
[tag_id] =>
[author] =>
[author_name] =>
[feed] =>
[tb] =>
[paged] => 0
[meta_key] =>
[meta_value] =>
[preview] =>
[s] =>
[sentence] =>
[title] =>
[fields] =>
[menu_order] =>
[embed] =>
[category__in] => Array
(
)
[category__not_in] => Array
(
)
[category__and] => Array
(
)
[post__in] => Array
(
)
[post__not_in] => Array
(
)
[post_name__in] => Array
(
)
[tag__in] => Array
(
)
[tag__not_in] => Array
(
)
[tag__and] => Array
(
)
[tag_slug__in] => Array
(
)
[tag_slug__and] => Array
(
)
[post_parent__in] => Array
(
)
[post_parent__not_in] => Array
(
)
[author__in] => Array
(
)
[author__not_in] => Array
(
)
[search_columns] => Array
(
)
[ignore_sticky_posts] =>
[suppress_filters] =>
[cache_results] => 1
[update_post_term_cache] => 1
[update_menu_item_cache] =>
[lazy_load_term_meta] => 1
[update_post_meta_cache] => 1
[nopaging] => 1
[comments_per_page] => 50
[no_found_rows] =>
[order] => DESC
)
[tax_query] => WP_Tax_Query Object
(
[queries] => Array
(
)
[relation] => AND
[table_aliases:protected] => Array
(
)
[queried_terms] => Array
(
)
[primary_table] => wp_posts
[primary_id_column] => ID
)
[meta_query] => WP_Meta_Query Object
(
[queries] => Array
(
[0] => Array
(
[key] => new_authors
[value] => "134"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "134"
[compare] => LIKE
)
[relation] => OR
)
[relation] => OR
[meta_table] => wp_postmeta
[meta_id_column] => post_id
[primary_table] => wp_posts
[primary_id_column] => ID
[table_aliases:protected] => Array
(
[0] => wp_postmeta
)
[clauses:protected] => Array
(
[wp_postmeta] => Array
(
[key] => new_authors
[value] => "134"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
[wp_postmeta-1] => Array
(
[key] => new_presenters
[value] => "134"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
)
[has_or_relation:protected] => 1
)
[date_query] =>
[request] => SELECT wp_posts.ID
FROM wp_posts INNER JOIN wp_postmeta ON ( wp_posts.ID = wp_postmeta.post_id )
WHERE 1=1 AND (
( wp_postmeta.meta_key = 'new_authors' AND wp_postmeta.meta_value LIKE '{b227b1edc2b5f4dd67ea6dc5aaad2d61b63521943fb5bdd7605cbb5159c90c25}\"134\"{b227b1edc2b5f4dd67ea6dc5aaad2d61b63521943fb5bdd7605cbb5159c90c25}' )
OR
( wp_postmeta.meta_key = 'new_presenters' AND wp_postmeta.meta_value LIKE '{b227b1edc2b5f4dd67ea6dc5aaad2d61b63521943fb5bdd7605cbb5159c90c25}\"134\"{b227b1edc2b5f4dd67ea6dc5aaad2d61b63521943fb5bdd7605cbb5159c90c25}' )
) AND wp_posts.post_type IN ('post', 'webinars') AND ((wp_posts.post_status = 'publish'))
GROUP BY wp_posts.ID
ORDER BY wp_posts.post_date DESC
[posts] => Array
(
[0] => WP_Post Object
(
[ID] => 31494
[post_author] => 53
[post_date] => 2023-11-17 09:37:25
[post_date_gmt] => 2023-11-17 15:37:25
[post_content] =>
Watch Now
Whether it's AWS, Azure or Google cloud, security teams face challenges such as misconfigurations, human error and weak infrastructures.
Watch our webinar for insights and real-world examples.
[wonderplugin_video iframe="https://youtu.be/yYrqf6MbjO8" lightbox=0 lightboxsize=1 lightboxwidth=1200 lightboxheight=674.999999999999916 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=1200 videoheight=674.999999999999916 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]
[post_title] => Cloud Pentesting Uncovered: Real Stories, Practical Solutions
[post_excerpt] =>
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => securelink-and-netspi-cloud-pentesting-uncovered
[to_ping] =>
[pinged] =>
[post_modified] => 2023-12-20 13:27:06
[post_modified_gmt] => 2023-12-20 19:27:06
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?post_type=webinars&p=31494
[menu_order] => 4
[post_type] => webinars
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[1] => WP_Post Object
(
[ID] => 30976
[post_author] => 91
[post_date] => 2023-10-09 11:36:47
[post_date_gmt] => 2023-10-09 16:36:47
[post_content] =>
Whether it's AWS, Azure or Google cloud, security teams face challenges such as misconfigurations, human error and weak infrastructures.
Join Director of EMEA Services Sam Kirkman and Senior Cloud Security Consultant Nick Lynch on this webinar for their takes on identifying vulnerabilities across the cloud, with helpful details on how our team assesses cloud infrastructures, finds gaps and helps remediate issues for a stronger security posture.
Key talking points:
- How to reduce organisational risk and improve cloud security
- Ways to identify vulnerabilities, credentials and misconfigurations
- Comparing cloud pentesting findings to other testing
- Real-world engagements and examples of exposures
- Benefits of cloud pentesting
Join NetSPI and SecureLink to discuss the “Harsh Truths of Security Testing.” Learn how you can use these findings to make a meaningful difference to your security, not just your budget.
Key takeaways:
- All penetration tests are not equal
- Why your expensive security tools will never be enough
- Threat actors use the same techniques which are rarely advanced or complex
[wonderplugin_video iframe="https://youtu.be/rpsQTDJyHe8" lightbox=0 lightboxsize=1 lightboxwidth=1200 lightboxheight=674.999999999999916 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=1200 videoheight=674.999999999999916 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]
[post_title] => Harsh Truths of Security Testing [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => securelink-harsh-truths-of-security-testing [to_ping] => [pinged] => [post_modified] => 2023-07-20 17:21:51 [post_modified_gmt] => 2023-07-20 22:21:51 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=webinars&p=30636 [menu_order] => 19 [post_type] => webinars [post_mime_type] => [comment_count] => 0 [filter] => raw ) [3] => WP_Post Object ( [ID] => 29190 [post_author] => 138 [post_date] => 2023-01-24 09:00:00 [post_date_gmt] => 2023-01-24 15:00:00 [post_content] =>While some teenagers play Call of Duty® with their friends, there are others more inclined to explore the dark side of the internet.
According to the Kaiser Family Foundation, children and teens ages 8-18 now spend 7.5 hours in front of a screen each day on average. And today, access to illicit content is more prevalent than ever through availability of resources, forums, and inquisitive thinking.
From vulnerability exposure to financial gain, teenagers, as tech natives, pose a huge risk to cybersecurity and are becoming more sophisticated in the type of hacks and attacks they attempt.
Just in the past year, there have been numerous major breaches that were led by young cyber adversaries. Bloomberg reported that a string of high-profile hacks against technology companies, including Microsoft and Nvidia, have been traced backed to a 16-year-old living at his mother’s house near Oxford, England. They allegedly belong to the notorious Lapsus$ hacking group. In September 2022, the City of London Police revealed that a 17-year-old had been arrested on suspicion of involvement in the recent cyberattacks targeting both Uber and Rockstar Games, according to reporting by Security Week.
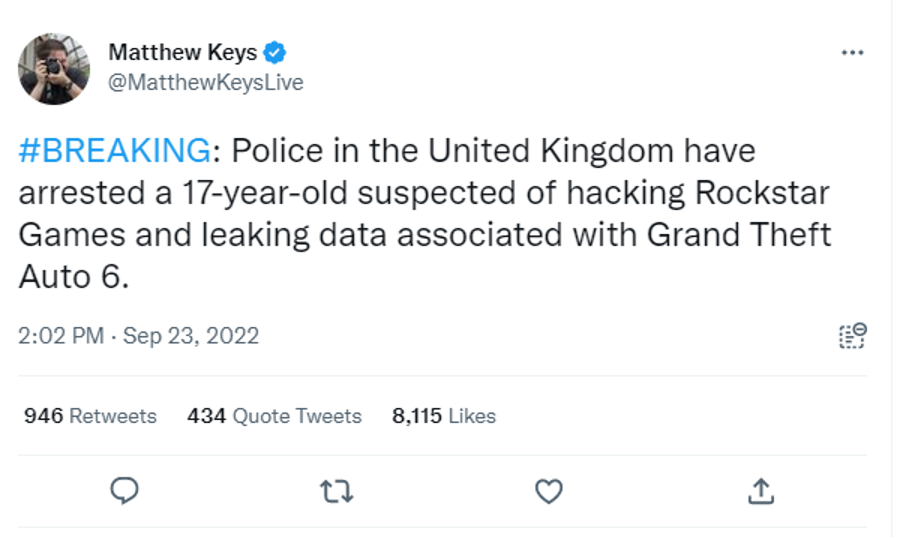
With the ever-growing prevalence of online gaming among teens, most children will be aware of ‘hackers’, even if it is within the context of a game. This opens the door to actively challenging systems, motivated to affect grades, create havoc, or derive financial gain and research into more serious hacking.
Even a basic search of how to hack will result in the discovery of some incredibly dangerous resources that could allow even untrained and inexperienced teenagers to cause issues. For only £7 a month, there are ethical hacking training program subscriptions that will teach users to properly utilise and understand those resources. With the amount of free time and growing independence during this stage of life, it is easy to upskill to a worrying and threatening level within a year.
Teenagers with an interest in hacking will often arrive at online forums where criminal hackers discuss their exploits and teach others how to achieve the same outcomes. We face a situation with the internet giving young adults knowledge and skills to cause damage, with little direction, governance, or consequence. It is no surprise that so many end up on the wrong side of the law.
What can be done?
Unfortunately, there are few meaningful outlets for skilled teens at the time of writing. Teens are considered too young to start building a career from their skills. Online “capture the flag” exercises can be fun, but rarely mirror real-world ethical hacking, or penetration testing. Bug bounty programs are equally unhelpful, as successful bug bounty hunters tend to be extremely experienced. Even talented teens are unlikely to find their curiosity satiated by these outlets alone.
Recommended Reading: Penetration Testing Services vs. Bug Bounty Programs
Naturally, they seek other opportunities to test their skills. Proof-of-Concept (POC) code for new vulnerabilities, known as “Zero Days”, can be tempting. Once a POC exists on the internet it’s a race against time for system owners to patch their systems or be hacked (see: Log4Shell).
Some POCs are “point and click”, taking only a few seconds to execute a sophisticated attack in a world where information is king. Stolen databases are worth good money to the right buyer. Even where teens may not knowingly steal and sell data from systems they successfully hack, just attempting to access a computer system without authorisation represents a breach of the Computer Misuse Act 1990. The maximum sentence for convictions under this legislation is life imprisonment.
Despite this, there seems to be a perception that people caught hacking are given government jobs rather than a criminal record, but that is rarely the case. Instead, those with a chequered past are more likely to face frequent rejection by employers in a demanding cybersecurity industry.
More needs to be done to get people on the right path from a young age. The cybersecurity industry, together with the national government, need to guide the next generation of cybersecurity professionals.
The introduction of nationally recognised certifications specifically for young people could be a great place to start. This would expose children to a positive path before they use their skills for nefarious purposes. Particularly talented young people could then progress to the certifications used by industry professionals, providing a structured path for continued development. Ultimately, people with the right skills and motivations will be welcomed into the industry to utilise their skills for good - whilst getting paid well to do so.
[post_title] => The Biggest Risks in Cyber: Curious Teenager Edition [post_excerpt] => A look at the risks curious teenagers pose to global security – and opportunities to guide them to a career in ethical hacking. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cyber-risks-teenagers [to_ping] => [pinged] => [post_modified] => 2024-01-11 12:43:34 [post_modified_gmt] => 2024-01-11 18:43:34 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29190 [menu_order] => 159 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) ) [post_count] => 4 [current_post] => -1 [before_loop] => 1 [in_the_loop] => [post] => WP_Post Object ( [ID] => 31494 [post_author] => 53 [post_date] => 2023-11-17 09:37:25 [post_date_gmt] => 2023-11-17 15:37:25 [post_content] =>Whether it's AWS, Azure or Google cloud, security teams face challenges such as misconfigurations, human error and weak infrastructures.
Watch our webinar for insights and real-world examples.
[wonderplugin_video iframe="https://youtu.be/yYrqf6MbjO8" lightbox=0 lightboxsize=1 lightboxwidth=1200 lightboxheight=674.999999999999916 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=1200 videoheight=674.999999999999916 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]
[post_title] => Cloud Pentesting Uncovered: Real Stories, Practical Solutions [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => securelink-and-netspi-cloud-pentesting-uncovered [to_ping] => [pinged] => [post_modified] => 2023-12-20 13:27:06 [post_modified_gmt] => 2023-12-20 19:27:06 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=webinars&p=31494 [menu_order] => 4 [post_type] => webinars [post_mime_type] => [comment_count] => 0 [filter] => raw ) [comment_count] => 0 [current_comment] => -1 [found_posts] => 4 [max_num_pages] => 0 [max_num_comment_pages] => 0 [is_single] => [is_preview] => [is_page] => [is_archive] => [is_date] => [is_year] => [is_month] => [is_day] => [is_time] => [is_author] => [is_category] => [is_tag] => [is_tax] => [is_search] => [is_feed] => [is_comment_feed] => [is_trackback] => [is_home] => 1 [is_privacy_policy] => [is_404] => [is_embed] => [is_paged] => [is_admin] => [is_attachment] => [is_singular] => [is_robots] => [is_favicon] => [is_posts_page] => [is_post_type_archive] => [query_vars_hash:WP_Query:private] => 64d1ce75b78466d26a49d5d1fec402b4 [query_vars_changed:WP_Query:private] => [thumbnails_cached] => [allow_query_attachment_by_filename:protected] => [stopwords:WP_Query:private] => [compat_fields:WP_Query:private] => Array ( [0] => query_vars_hash [1] => query_vars_changed ) [compat_methods:WP_Query:private] => Array ( [0] => init_query_flags [1] => parse_tax_query ) )