E-Commerce Trends During COVID-19 and Achieving PCI Compliance
Online Shopping Behavior and E-Commerce Transformation
By this point it’s clear that organizations and every individual has to make changes and adapt their day-to-day activities based on the weeks of lock-down that everyone has faced due to the Coronavirus.
All of a sudden, there’s a surge of people using mobile applications and online payments to order food, medicine, groceries, and other essential items through delivery. Due to social distancing requirements that are in place, the interactions between retailers and consumers have shifted drastically. We all know that people are heavily dependent on their mobile devices, even more so today than ever before. New studies show that “72.1% of consumers use mobile devices to help do their shopping” and there’s been a “34.9% increase year over year in share of consumers reporting online retail purchases.”
Businesses have been drastically impacted during the pandemic, and they’re also adapting to be able to conduct business online more than ever before. In these efforts, there’s been an increase in using online payments through the use of credit card transactions because they are preferred since they’re contact-less compared to cash transactions (which add a higher likelihood of the Coronavirus spreading through touch).
Given the increased use of online credit card payments, organizations need to ensure that they’re compliant with the Payment Card Industry (PCI) Data Security Standard – referred to as PCI DSS. The current version of the PCI-DSS is version 3.2.1 which was released in May 2018.
The Spirit of PCI DSS
PCI DSS is the global data security standard which all payment card brands have adopted for anyone that is processing payments using credit cards. As stated on their website, “the mission is to enhance global payment account data security by developing standards and supporting services that drive education, awareness, and effective implementation by stakeholders.”
Payment card data is highly sensitive, and in the case cardholder data is stolen or compromised, it’s quite a hassle to deal with that compromise. Attackers are constantly scanning the internet to find weaknesses in systems that store and process credit card information.
One well-known credit card breach was in late 2013 when a major retailer, had a major breach. This attack brought to the foreground the importance of ensuring proper segregation of systems that process credit card payments from other systems that may be on the same network.
PCI DSS wants to ensure that any entity that is storing or processing credit card information are following the minimum bar when it comes to protecting and segregating credit card information.
I am not going to go into detail about each and every PCI DSS requirement, but focus this post around how we at NetSPI help our clients with their journey towards PCI compliance.
NetSPI’s Role in Our Clients’ PCI Compliance Journey
First of all, it’s important to note that at the moment, NetSPI has made the business decision not be a PCI “Approved Scanning Vendor” (ASV) or a PCI “Qualified Security Assessor” (QSA). You can find the PCI definitions for these at the PCI Glossary. Given NetSPI’s business objectives, our focus is on deep dive, high quality technical offerings instead of having an audit focus that is required in order to be an ASV or a QSA.
That being said, we are extremely familiar with PCI DSS requirements and work with some of the largest banks and financial institutions to enable them to become PCI compliant (and meet other regulatory pressures) by helping them in their efforts to develop and maintain secure systems and applications, and regularly testing their security systems and processes.
We’ll go deeper into some of the specific PCI requirements that we work closely with our customers on, and describe our service offerings that are leveraged in order to satisfy the PCI requirements. In almost all cases, NetSPI’s service offerings go above and beyond the minimum PCI requirements in terms of technical depth, scope, and thoroughness.

PCI Requirements and Services Mapping
PCI at a high level provides a Security Standard that’s broken down as shown in the table below that’s been published in their PCI DSS version 3.2.1.
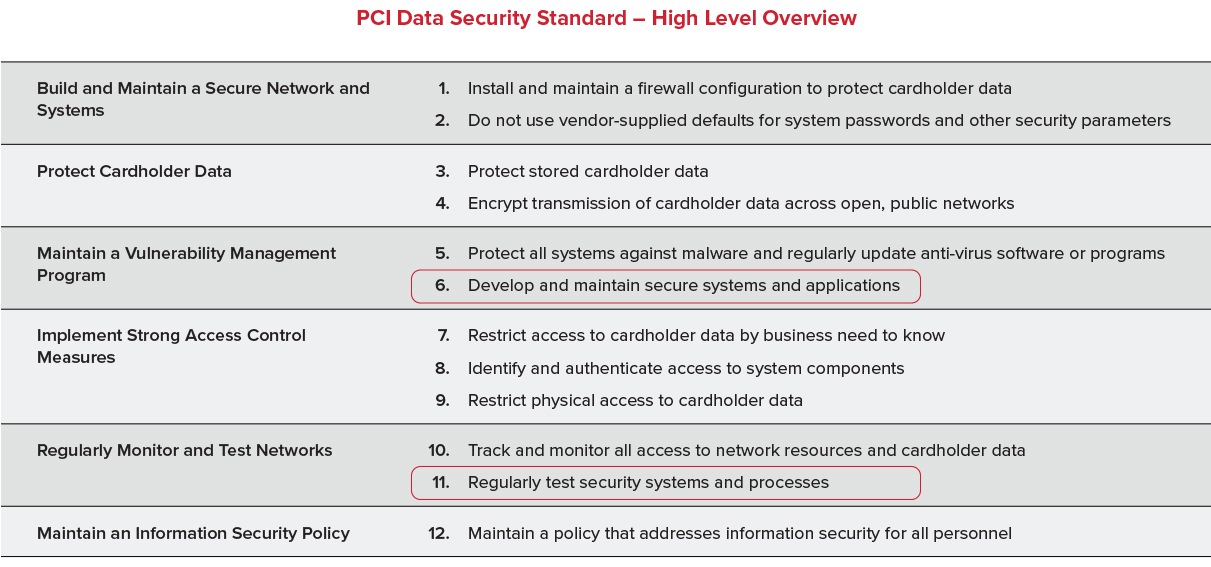
PCI DSS Requirement 6.3
Incorporate information security throughout the software-development lifecycle.
NetSPI Offerings Leveraged by Clients
NetSPI is an industry-recognized leader in providing high quality penetration testing offerings. NetSPI’s offerings around Web Application, Mobile, and Thick Client Penetration Testing services are leveraged by clients to not only satisfy PCI DSS Requirement 6.3, but also go beyond the PCI requirements as elaborated on in their requirement 6.5.
PCI DSS Requirement 6.5
Verify that processes are in place to protect applications from, at a minimum, the following vulnerabilities:
- Injection Flaws
- Buffer Overflows
- Insecure Cryptographic Storage
- Insecure Communications
- Improper Error Handling
- Cross-site Scripting
- Cross-site Request Forgery
- Broken Authentication and Session Management
NetSPI Offerings Leveraged by Clients
NetSPI’s Web Application, Mobile, and Thick Client Penetration Testing services go above and beyond looking for vulnerabilities defined in the list above. The list of vulnerabilities in this particular requirement is heavily driven by the OWASP Top Ten list of vulnerabilities. NetSPI’s service offerings around Application Security provides at a minimum OWASP Top Ten issues, but typically goes above and beyond the OWASP Top Ten list of vulnerabilities.
PCI DSS Requirement 6.6
For public-facing web applications, address new threats and vulnerabilities on an ongoing basis and ensure these applications are protected against known attacks by either of the following methods:
- Reviewing public-facing web applications via manual or automated application vulnerability security assessment tools or methods, at least annually and after any changes
- Installing an automated technical solution that detects and prevents web-based attacks (for example, a web application firewall) in front of public-facing web applications, to continually check all traffic.
NetSPI Offerings Leveraged by Clients
NetSPI’s Web Application Penetration Testing offerings are highly sought after by our clients. In particular, at NetSPI we work closely with seven of the top 10 banks in the U.S., and are actively delivering various levels of Web Application Penetration Testing engagements for them. Customers continue to work with us because of the higher level of quality that they see in the output of the work we deliver, which is typically credited to the use of our Penetration Testing as a Service delivery model which is enabled by our Resolve ™ platform.
PCI DSS Requirement 11.3
Implement a methodology for penetration testing:
- A penetration test must be done every 12 months.
- The penetration testing verifies that segmentation controls/methods are operational and effective, and isolate all out-of-scope systems from systems in the CDE.
- Methodology includes network, server, and application layer testing.
- Includes coverage for the entire CDE perimeter and critical systems. Includes testing from both inside and outside the network.
NetSPI Offerings Leveraged by Clients
NetSPI provides both Internal and External Network Penetration Testing services. When customers request an assessment that they want to leverage the results to satisfy PCI requirements, NetSPI provides customers with deliverables that are tailored to be provided to our client’s QSA to satisfy PCI requirements. In cases where the Cardholder Data Environment (CDE) is located in the Cloud, then NetSPI Cloud Penetration Testing goes above and beyond the minimum PCI Stanrdard’s testing requirements.



