Embedded Penetration Testing
Identify embedded system vulnerabilities in a penetration test across multiple disciplines. We look for security issues at any stage of embedded development that may affect each layer of the device.
Improve Embedded Device Security
As more devices are connected to the internet, embedded security practices help reduce cybersecurity risk in an organization’s network. Embedded devices could include connected HVAC systems, dishwashers, routers, POS terminals, fitness trackers, and much more.
During NetSPI’s embedded pentesting service, we will identify vulnerabilities across multiple disciplines, including hardware, network, wireless, secure design review, thick client applications, system hardening, and, in some cases, mobile. We evaluate the embedded networks, systems, and applications from the perspective of an anonymous user – following both manual and automated processes.
What Does NetSPI Test?
- Firmware Analysis
- Tamper Protection
- Reverse Engineering
- Hardware Testing
- Chip Removal
- Wireless Configuration
- Principle of Least Privilege
- Thick Client Applications
- Secure Storage
- Peripheral Security
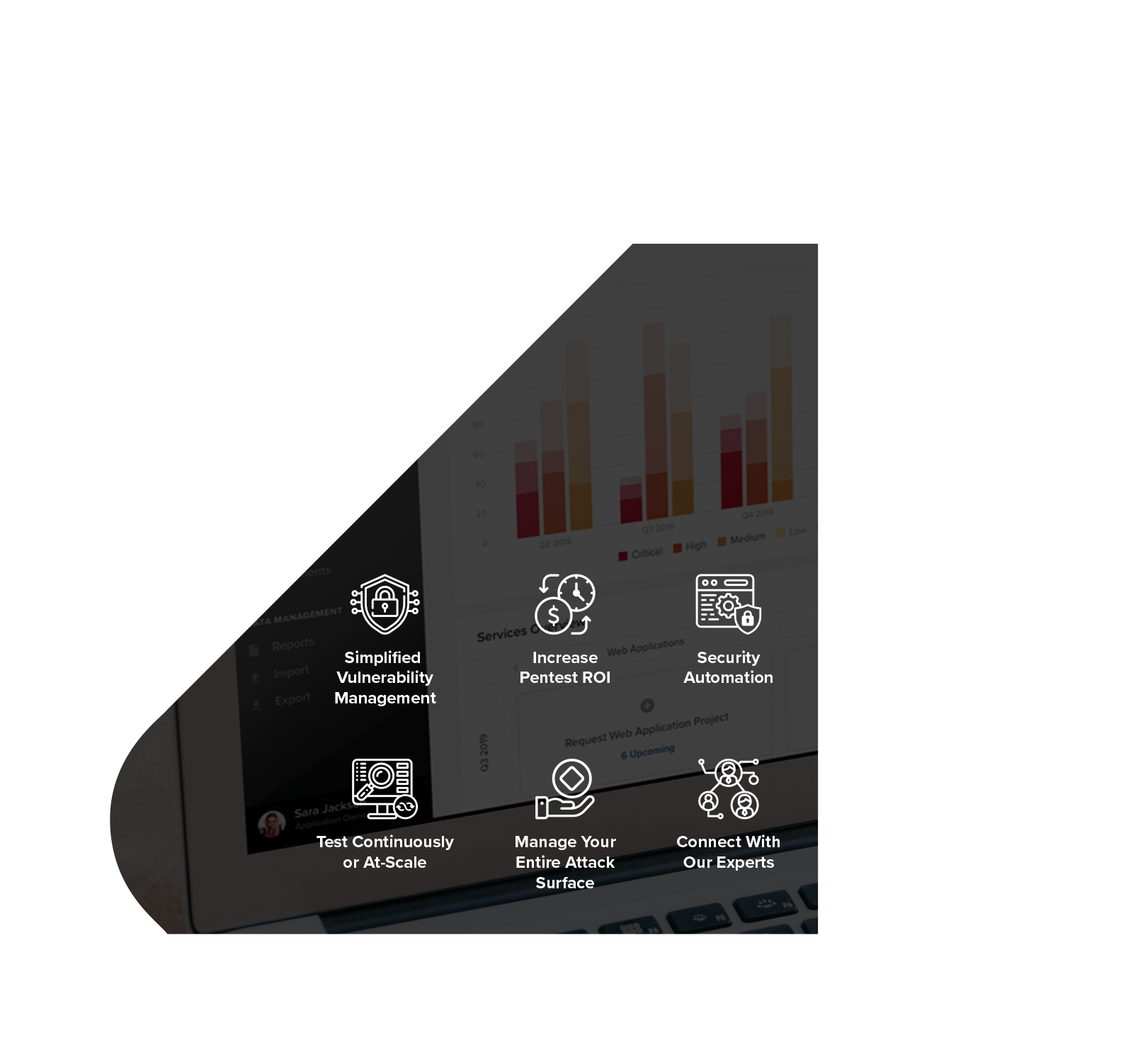
Powered by Resolve™
Embedded pentest engagements are managed and delivered through Resolve, NetSPI’s vulnerability management and orchestration platform. Resolve elevates your vulnerability management and pentesting program.

Pentesting Research and Tools
Learn about penetration testing on our blog, our open source penetration testing toolsets for the infosec community, and our SQL injection wiki.
